
This post kicks off a three part a series on blockchain technology. Previously, I discussed the development of blockchain networks, detailing the history of both the modern internet and blockchain technology.
This part of the series will focus on how the technology works, including one post on how protocols work and another on ICOs, DAPPs and DAOs. The next part of the series will then highlight a few of the most attractive areas for investment in the space. Alright, enough of the overview, let’s dive in!
So why are we starting with protocols? We’re starting with protocols because they are the fundamental breakthrough of blockchain technology. When Satoshi Nakamoto published his paper in 2008, the true technological innovation of bitcoin was the blockchain protocol that powered the bitcoin network. However, before we get into the nitty-gritty of blockchain protocols, I think it’s helpful to start with the protocols that power the modern internet (blockchain protocols wouldn’t be possible without them). If you have a solid understanding of these, feel free to skip ahead!
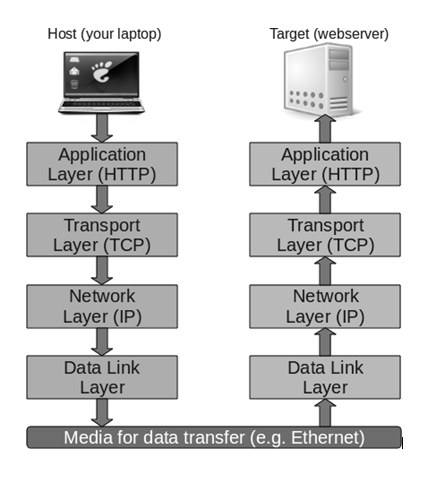
The first question to ask is: what is a protocol? A protocol is the method by which data is sent from one computer to another over the internet. The three protocols that power the modern internet are the HyperText Transfer Protocol (“HTTP”), Transmission Control Protocol (“TCP”), and Internet Protocol (“IP”). The TCP and IP are the protocols that help to route information across the network and HTTP is an application-level protocol for web browsers. If you’re a little bit confused by what these terms mean, that’s totally understandable. Let’s break it down
Source: https://www.researchgate.net/ | Uploaded by Stan Mierzwa
TCP / IP
The Transmission Control Protocol and Internet Protocol make up what is known as the “internet protocol stack”. This is due to the fact that they are the protocols that actually route information across a network. The graphic to the left provides a good visual of how this works. The Transmission Control Protocol takes information from your applications, breaks that information down into smaller data packets, adds headers so that the information can be repackaged in the recipient’s computer, and then sends those data packets to the Internet Protocol. The IP then takes those data packets, adds IP headers (which includes the IP address of both the sender and the receiver) and routes that information across the internet. Once the data packets arrive at the recipient’s computer, the recipient’s IP passes them along to the TCP, which repackages them and sends them to the appropriate application.
HTTP
Like I mentioned above, the HyperText Transfer Protocol is an application-level protocol. That means it is a protocol that sends data to the TCP / IP protocol stack (which then routes it across the network). HTTP is the protocol that allows web browsers to communicate with web servers. Let’s look at an example. When you type a URL into Google Chrome, the web browser connects to a Domain Name Service and identifies what IP address the website is being hosted at. After identifying the website, the browser sends an HTTP request to the server (via the TCP / IP protocol stack). If the page exists, then the web server sends the content back to the browser and the browser displays it on the requester’s screen. If the page does not exist, then the server sends back an HTTP 404 error saying that the page does not exist (I’m guessing we’ve all experienced this annoying error before). While HTTP is one type of application protocol, it certainly isn’t the only one. There are a number of protocols that we use on a daily basis, including the Simple Mail Transfer Protocol, which enables email communication.
Alright hopefully we didn’t lose you there! I think it’s helpful to start with the current internet protocol stack because blockchain protocols are actually built on top of TCP / IP, similar to application protocols like HTTP. If you’re looking for a more detailed overview of internet protocols, check out this awesome white paper written by Rus Shuler. Now, let’s move on and dig into into how blockchain protocols work.
As we discussed, protocols are a method for sending information across a network. Blockchain protocols approach this a little differently than the traditional internet protocols. Although not every blockchain protocol is the same, they share a few defining characteristics. Those characteristics include (i) distributed ledgers, (ii) encryption, (iii) consensus algorithms, and (iv) integrated blocks of data. Let’s briefly discuss how each of these elements work.
Distributed Ledgers
Distributed ledgers are probably the best place to start. So what is a distributed ledger? A distributed ledger is a decentralized database that is shared across several locations or network participants. Said differently, a distributed ledger is a peer-to-peer network where every piece of information / transaction is shared across the network and stored by each network participant (or “node”).
Distributed ledgers directly contrast the client-server architecture that powers the modern internet. A client-server architecture is a model where information is stored on central servers and may be requested by users (known as “clients”). For example, institutions like Facebook, Google and Amazon have large, centralized servers where they store their users’ transaction histories, personal information, etc. Clients (aka everyday users like you and me) tap into those servers through HTTP requests, which we discussed above. Peer-to-peer networks differ from the client-server model because they don’t have an intermediary that acts as a central point of storage. Rather, each connected node acts as both a client and a server.
So why would we do this? What’s the benefit? The benefit of using a distributed ledger rather than a centralized databases is that there is no single point of failure, which decreases the odds that a network is hacked / information is lost. In addition to that, there is not a single entity that owns the data stored on the network. This means that nobody is monetizing that data or using it in a way that the user doesn’t approve of. As a result, users have control over their data and can decide what they want to do with it. In the future, network participants may actually be able to sell their data if they want to. For example, if you store your search history on a blockchain version of Google, then you may be able to sell that search history to advertisers. Advertisers would pay you for the ability to send you targeted adds rather than an intermediary like Google. However, I’m getting ahead of myself as this has yet to become a reality.
Okay, one more point on distributed ledgers. I’m guessing you’re thinking, THIS IS INSANE. It’s a total invasion of privacy. Why would I store my personal information on a bunch of strangers’ computers? Luckily, blockchain protocols have a solution for this: encryption. Blockchain protocols incorporate advanced encryption methods to conceal both the identities of network participants and the content of transactions, which is what we’re going to cover in the next section.
>> An introduction to blockchain. Part two: Encryption
